What Is Ping Spoofing? That’s what we’re uncovering in the following article. Along with the following:
- How To Detect Ping Spoofing?
- How To Mitigate Ping Spoofing?
- What Factors Do Ping Spoofing Depend On?
Let’s throw some light on the above-listed queries in detail.
Ping Spoofing is illegal, and to make a direct spoof to make one’s pink rank higher is also banned in most servers. This is because the packet we send to the server automatically changes when we use this, making it illegal.
In addition, it simulates high ping fluctuations to create a fake identity of yours so that the servers do not recognize us.
People use ping spoofing to manipulate data they have to send to a particular server. It becomes complex for the server to detect hacking or simply lagging when they use ping spoofing.
Generally, people who use it make the pings look bad for confusing the servers and retaining their fake identities. So, now, let’s learn about this in detail.
What Is Ping Spoofing?

A program that transmits the ICMP ping packets to the servers that make it look like the generation is from another source is ping spoofing. The system receiving the ping can reply to it, but it will be transmitted to another third-party machine.
In short, if you send a thousand ping packets to legal servers using the ping spoofing technique, the server will receive non-requested replies from a thousand different sources.
Thus, it overloads the packet procession engine and the channel. Thereby, risking crashing the machine destroying all its essential data. The hacker remains unseen to the server because the thousands of multiple sources that replied to that ping are trustful sources who did it unknowingly.
A ping spoofer can also ask for various large-sized files and remains invisible to the server to block them.
What Is Ping Spoofing In Minecraft?

It can help you fake your identity, but it does not affect the gameplay of Minecraft in any possible way. Other players might think you are having severe ping issues while playing the game, making it difficult for them to attack you.
In Minecraft, many players often use this spoofing. Although it demonstrates an unstable connection to other users, you can retain the most vital connection to the server while you use it.
You cannot get hit by other players when you use this spoofing, making it easier to take advantage of other players in Minecraft. However, high ping takes a longer time to register the signals.
It makes the server think you have high ping issues when you have many pings. Thus, it attracts the server towards your gaming profile, and people often use it while playing Minecraft to blame all the lagging hits on this.
How To Detect It?
In Minecraft, the easiest way of detecting this spoofing would be to notice when the person supposedly having high ping issues is not lagging. Instead, they continuously face high pings, so the absurd number of pings can detect the spoofing.
However, it is also mentioned-worthy that only if a user employs this spoofing to an extreme degree can we see them. If they use it moderately, then it remains genuinely undetectable.
The detection also depends upon the type of ping packet sometimes. For example, some ping packets can be blocked, such as the keepAlive packet, and when the user stops it, he can still receive other ping packets but not the blocked ones.
You can also detect it by sending a ping packet from your end to the client, knowing how fast or slow he can reply. When you get the reply, you will tally it with your estimated time, and if it does not match, you will be able to detect the ping spoofing.
High pings generally take a much longer time to send. Thus, you can try to detect it by checking whether the server is lagging data. However, if the information is not weakening, high pings are present, making the route impossible to detect. Furthermore, it will end up confusing the ping spoof detector.
How To Mitigate Ping Spoofing?
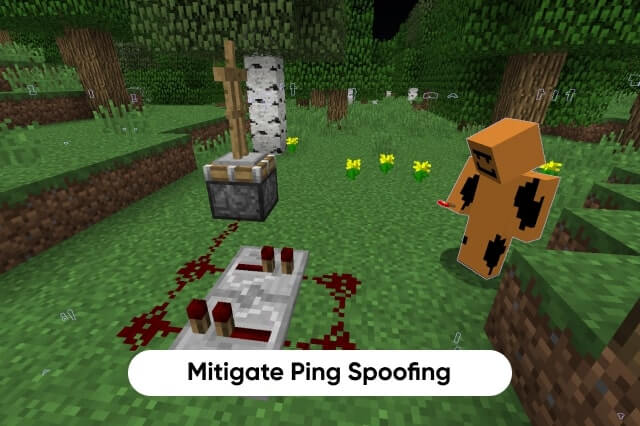
Ping Spoofing can send disruptive signals to a server making it less secure and somewhat impossible to operate. If you want to protect your machine from ping spoofing, you only have to reconfigure your perimeter’s firewall.
It will no longer receive the ping requests and will block pings originating in other networks except yours. This technique will blanket block the ping requests.
However, the complications of blanket blocking the ping requests can also be disastrous. If the server has an issue, it will be impossible to detect that because all the ping requests are already blocked.
You can always use the Imperva DDoS protection for blanket blocking purposes. It can limit the size of each ping request and restrict the rate at which it is supposed to be received.
What Factors Do Ping Spoofing Depend On?
First, you must know “what is ping spoofing.” Then you can proceed to know the factors that ping spoofing depends on. Ping spoofing depends upon many factors, and those factors determine to what extent ping spoofing can hurt your server.
The quality of the internet service provider is a significant factor here. Every internet service provider varies from one another depending on a couple factors. Such as latency, speed, reliability, price, data availability, etc.
Thus, the stronger these factors will be in an ISP, the less chance you will be affected by ping spoofing.
The firewall configuration is also an essential factor. Your firewall checks all the data packets your computer is sending and receiving. The firewall configuration needs to be strong, so the internet connection speed does not slow.
If you are a gamer, you can change the firewall settings in your game. This stops the server from treating the game as an intervention.
It also depends upon your geographic location and the distance between your machines. And the server whether you will receive high ping requests.
For example, if your server is located near your device. You will be less likely to be affected by ping spoofing.
Conclusion
Hence, this is all about what is ping spoofing. We would like to conclude that ping spoofing is illegal, so you better stop doing it if you already do it.
People who are affected due to ping spoofing can update your firewall configuration. Because only that will protect your machine the most from these high ping requests.
It is almost impossible to detect ping spoofing unless someone uses it excessively, so you are affected by it; then look for the loopholes mentioned above to identify a ping spoofing.
You May Also Like: